IT solutions
What is CrowdStrike, the Software Company Behind Worldwide Outages?
the Software Company Behind Worldwide Outages
29. 7. 2024
Introduction
In the rapidly evolving digital landscape, cybersecurity stands as a critical pillar for protecting sensitive information and maintaining operational continuity. Among the prominent players in the cybersecurity industry is CrowdStrike, a company renowned for its cutting-edge solutions and comprehensive approach to threat detection and response. Recently, CrowdStrike found itself at the center of attention due to a series of worldwide outages. This article delves into the technical intricacies of the cybersecurity vulnerabilities that were exploited, shedding light on what went wrong and how it was addressed.
What is CrowdStrike?
CrowdStrike, founded in 2011 by George Kurtz and Dmitri Alperovitch, is a leading provider of cloud-delivered endpoint protection. The company is headquartered in Sunnyvale, California, and has garnered a reputation for its innovative Falcon platform, which leverages artificial intelligence (AI) and machine learning to detect and prevent threats in real-time. With a client base that includes major corporations and government entities, CrowdStrike plays a pivotal role in safeguarding digital infrastructures across the globe.
CrowdStrike's Approach to Cybersecurity
Overview of CrowdStrike Falcon Platform
CrowdStrike Falcon is an advanced cybersecurity platform that integrates next-generation antivirus, endpoint detection and response (EDR), and managed threat hunting. By harnessing AI and behavioral analytics, Falcon provides unparalleled visibility and proactive defense against sophisticated cyber threats.
Key Technologies and Methodologies
The Falcon platform employs a combination of AI, machine learning, and behavioral analysis to identify and mitigate threats. Its cloud-native architecture allows for rapid deployment and scalability, ensuring comprehensive protection across diverse environments. Additionally, CrowdStrike's threat intelligence feeds enrich the platform with real-time data, enabling more accurate and timely threat detection.
Importance of Threat Intelligence and Machine Learning
Threat intelligence and machine learning are cornerstones of CrowdStrike's strategy. By continuously analyzing vast amounts of data, Falcon can identify patterns and anomalies indicative of malicious activity. This proactive approach not only enhances detection capabilities but also reduces the time required to respond to incidents, thereby minimizing potential damage.
Understanding Cybersecurity Vulnerabilities
Definition and Types of Cybersecurity Vulnerabilities
Cybersecurity vulnerabilities are weaknesses or flaws in a system that can be exploited by malicious actors to gain unauthorized access, disrupt operations, or steal sensitive data. These vulnerabilities can arise from software bugs, misconfigurations, weak passwords, or unpatched systems.
Common Vulnerabilities in Enterprise Environments
In enterprise environments, common vulnerabilities include unpatched software, outdated systems, insufficient access controls, and lack of employee training on cybersecurity best practices. These weaknesses can provide entry points for attackers, leading to significant security breaches.
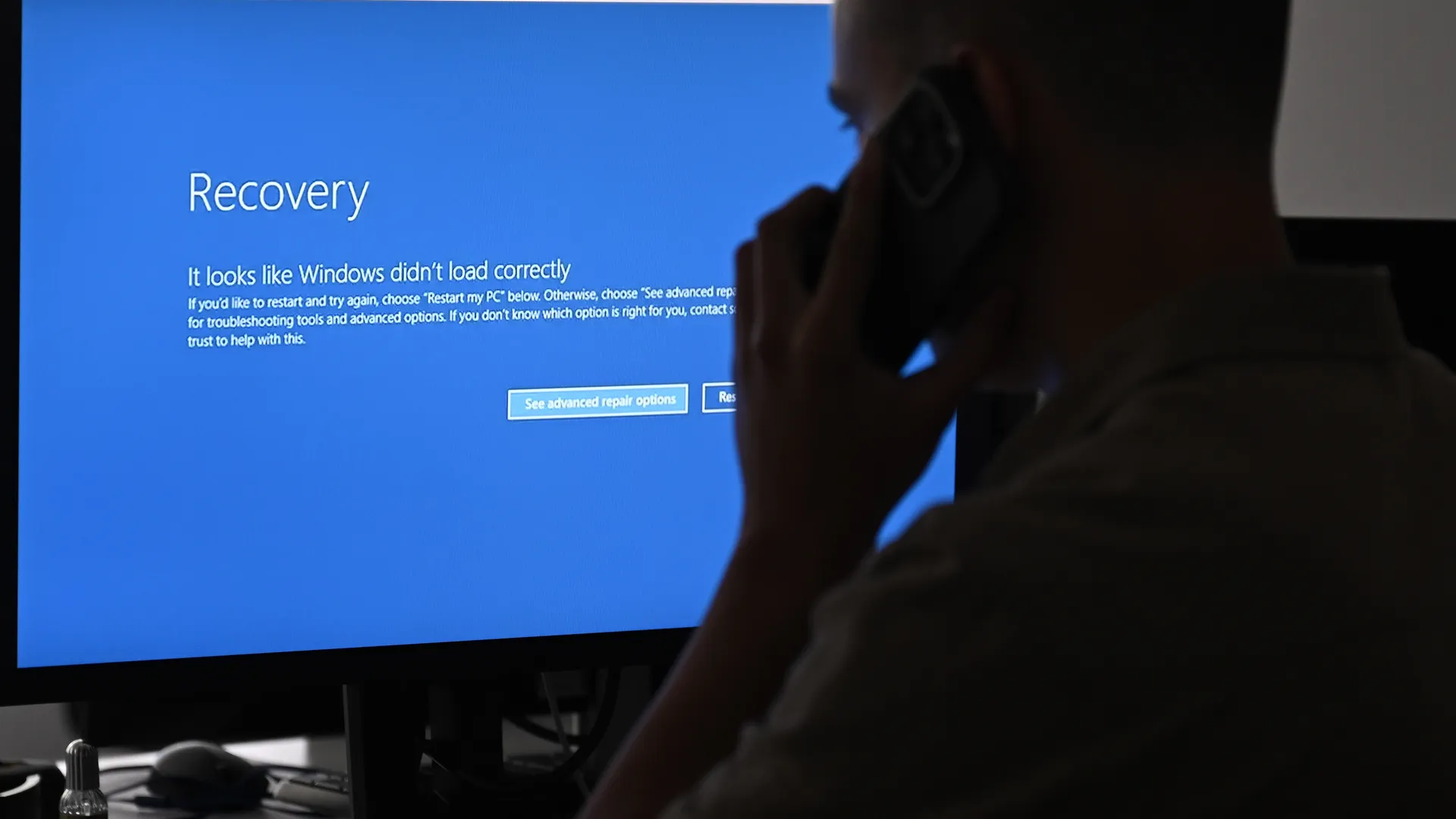
Recent Worldwide Outages Linked to CrowdStrike
Summary of the Incidents
The recent worldwide outages attributed to CrowdStrike stemmed from a series of sophisticated cyberattacks that exploited vulnerabilities within the company's infrastructure. These incidents disrupted services for numerous organizations, highlighting the critical nature of robust cybersecurity measures.
Impact on Businesses and Services
The outages had far-reaching impacts, causing operational disruptions, financial losses, and reputational damage for affected businesses. The incidents underscored the importance of having resilient cybersecurity strategies in place to mitigate the effects of such attacks.
CrowdStrike's Response and Mitigation Efforts
In response to the outages, CrowdStrike launched comprehensive investigations to identify and address the exploited vulnerabilities. The company also implemented enhanced security measures, communicated transparently with clients, and provided ongoing support to mitigate the impact of the incidents.
Technical Analysis of the Vulnerabilities Exploited
Detailed Description of the Specific Vulnerabilities
The attacks on CrowdStrike exploited multiple vulnerabilities, including those within the Falcon platform and its cloud infrastructure. These vulnerabilities allowed attackers to bypass security controls, gain unauthorized access, and execute malicious actions.
How Attackers Exploited These Vulnerabilities
Attackers leveraged advanced techniques such as zero-day exploits, spear-phishing campaigns, and privilege escalation to exploit the identified vulnerabilities. These methods enabled them to infiltrate CrowdStrike's defenses and compromise critical systems.
Technical Implications of These Exploits
The technical implications of these exploits were significant, revealing potential weaknesses in CrowdStrike's security posture. The incidents highlighted the need for continuous monitoring, timely patching, and robust incident response strategies to address emerging threats effectively.
Vulnerability: Falcon Sensor Bypass
Explanation of Falcon Sensor
The Falcon Sensor is a lightweight agent deployed on endpoints to collect data and enforce security policies. It plays a crucial role in detecting and mitigating threats at the endpoint level.
How the Bypass Was Achieved
Attackers identified and exploited a flaw in the Falcon Sensor's architecture, allowing them to bypass its detection capabilities. By manipulating certain aspects of the sensor's operation, they were able to execute malicious code undetected.
Steps Taken to Address This Issue
To address the Falcon Sensor bypass, CrowdStrike released a series of updates and patches to fortify the sensor's defenses. Additionally, the company enhanced its threat detection algorithms to better identify and respond to similar attack vectors in the future.
Vulnerability: Cloud Infrastructure Exploits
Overview of Cloud Vulnerabilities
Cloud infrastructure vulnerabilities arise from misconfigurations, inadequate access controls, and software bugs. These weaknesses can be exploited to gain unauthorized access, disrupt services, or exfiltrate data.
Specific Exploits Used Against CrowdStrike's Infrastructure
Attackers exploited misconfigurations and vulnerabilities within CrowdStrike's cloud infrastructure, enabling them to bypass security controls and access sensitive systems. These exploits were executed using advanced techniques that leveraged cloud-specific attack vectors.
CrowdStrike’s Measures to Strengthen Cloud Security
In response to the cloud infrastructure exploits, CrowdStrike implemented stricter access controls, conducted comprehensive security audits, and reinforced its cloud security posture. The company also enhanced its monitoring capabilities to detect and respond to suspicious activities more effectively.
Vulnerability: Endpoint Security Flaws
Details of Endpoint Security Vulnerabilities
Endpoint security vulnerabilities include weaknesses in the software, configurations, and user practices that protect individual devices. These vulnerabilities can be exploited to gain control over endpoints and access sensitive data.
Methods Used by Attackers to Exploit These Flaws
Attackers used techniques such as malware deployment, phishing, and zero-day exploits to compromise endpoint security. These methods enabled them to infiltrate endpoints, escalate privileges, and move laterally within networks.
Improvements Made to Endpoint Security
To improve endpoint security, CrowdStrike rolled out updates to its Falcon platform, enhanced its threat detection capabilities, and provided additional training and resources to clients. These measures aimed to bolster endpoint defenses and reduce the risk of future breaches.
Conclusion
CrowdStrike's experience with recent worldwide outages underscores the ever-present threat of cybersecurity vulnerabilities and the critical need for robust defenses. By understanding and addressing the specific vulnerabilities exploited by attackers, organizations can strengthen their security posture and better protect themselves against future incidents. As the cybersecurity landscape continues to evolve, continuous vigilance and proactive measures will be essential to safeguarding digital assets and maintaining operational resilience.
FAQs
What is CrowdStrike known for? CrowdStrike is known for its advanced cybersecurity solutions, particularly its Falcon platform, which provides real-time threat detection and response.
How did CrowdStrike handle the recent outages? CrowdStrike responded by investigating the incidents, implementing enhanced security measures, and providing transparent communication and support to affected clients.
What specific vulnerabilities were exploited? The vulnerabilities exploited included those within the Falcon Sensor, cloud infrastructure, and endpoint security, allowing attackers to bypass defenses and execute malicious actions.
How can businesses protect themselves from similar vulnerabilities? Businesses can protect themselves by implementing robust security measures, conducting regular security audits, ensuring timely patching, and providing ongoing training for employees.
What is the future of CrowdStrike in the cybersecurity landscape? CrowdStrike is expected to continue its leadership in the cybersecurity industry, focusing on innovation, enhanced threat detection, and proactive defense strategies to address emerging threats.
Written by: Matthew Drabek & Mohamed Ismail
For our Services, feel free to reach out to us via meeting…
Please share our content for further education